What is a CISO?
As a chief information security officer (CISO) we act as senior-level executive responsible for establishing and maintaining the enterprise vision, strategy, and program to ensure information assets and technologies are adequately protected. The CISO directs staff in identifying, developing, implementing, and maintaining processes across the enterprise to reduce information and information technology (IT) risks. We respond to incidents, establish appropriate standards and controls, manage security technologies, and direct the establishment and implementation of policies and procedures. As a CISO we are also usually responsible for information-related compliance (e.g. GDPR), and help ensure the company remains within the lines of the law.
Having a CISO or an equivalent function in organizations has become standard practice in business, government, and non-profits organizations.
How can we help you?
Hiring a CISO as an internal resource is both challenging (min 6 months) and very expensive (+150K) because there is a lack of specialists on the market. Reality is that most companies don't need a full time employee for this role which results in inefficient use of your budgets. At the same time, for start-ups or big companies, there is no way around security and complying with the strict privacy regulations. Would it not be better if you could save some of that budget and use it instead for actual security controls that you really need?
That's where we can help you! We offer at least 2x the results of a regular CISO with clear objectives and a guaranteed raise of your security maturity in no time!
Before you start working with us, we'll make sure we align on following points:
-
Why you need a CISO
-
How to ensure you don't overspend or underspend on security
-
Clarify the ROI from a solid security program
-
Validate our experience with your needs
-
Ensure we get the management commitment (not just involvement) for a security program
-
How security is not a blocker, but an enabler for your business

What is the purpose?
- Protect secrets/assets
-
Competitive advantage
-
Business reputation
-
Business continuity
-
Report to management
-
Respond to incidents
-
Global governance

What is the process?
-
Assessment of core security areas below
-
Security program development
-
Security program
implementation

What is the outcome?
-
Information security management system
-
Asset/Risk mapping
-
Stakeholder prioritisation
-
Measured processes & controls
-
Security maturity improvement
-
Roles & responsibilities
-
Compliance & certifications
-
Education of employees
Core security areas
As part of a security program we'll focus on the different core security areas listed below to ensure we ask the right questions and take a pragmatic risk based prioritisation of efforts in line with your business requirements, risk appetite and security budget.
To manage your security & compliance we use our in house developed GRC & ISMS platform
Password & Access management
Have your critical application passwords leaked on the internet? Does your staff have a password management in place? Do you know who has access to what and why? Are people reusing passwords? Are you implementing the principle of least privilege/need to know? Do you have a single sign on solution in place?
Cloud security
What if your G Suite or Microsoft 365 data got stolen, or simply (accidentally) removed. Can this be restored? Are your Amazon Web Services or Azure resources properly protected? Are you profiting from all security services already included in your cloud services? Are your critical business services protected against denial of service attacks?
Communication security
What would a competitor do with the information in your mailbox? Are your current communication flows compliant with privacy regulation? Do you have a backup of all your mails? What is your retention policy on personal data? Can the data you send be intercepted/altered in transit?
Security policies & procedures
Does your staff know and understand the rules? Have you discovered the power these can give to govern your company? Are you able to reply to partners on what you actually enforce, or is it more an unwritten rule? Do you have an information security management system that documents all your security/compliance efforts?
Endpoint security
Are the computers and mobile devices in use by your staff properly protected? Are you informed when one of your endpoints gets infected (or when it is attempted). Can you isolate this device to prevent spreading to other devices? Is the data on centrally stored, or will your data also be lost when devices compromised? Does your staff have illegal software installed (with most probably some backdoors)?
Secure remote access
How does staff access your corporate data? Are devices properly hardened for remote work? Do you have clear rules on how private/company devices can be mixed. Is staff aware that "free" WIFI in hotels or pubs are a huge security risk?
Attack mitigation
Are you tracking (unauthorized) access to your systems. Can you automatically block common network/system attacks? Do you have a documented security baseline to know what is normal and what is not? Do you know when your website starts loading scripts from other sources than intended? Are you able to quickly block specific users or malicious actor IPs from your website?
Security awareness training
Has all staff received appropriate and easy to understand security and compliance awareness training? Does your staff know how to report security incidents and why a timely way of doing so is important? Does your staff consider security as a IT responsibility, or is this a shared mentality?
Vulnerability management
Is your team informed on zero-day vulnerabilities? Is your source code automatically scanned and your teams continuously informed about (new) vulnerabilities or wrong coding practices? Do your systems get regular security updates?
Securing IT infrastructure
Is your internal systems properly secured? Will you be notified if there is suspicious activity? Are there unidentified devices plugged in your network/servers? Do you have an asset inventory? Are you making backups of the right things? What's the impact on your business if your core services go down on peak moments?
Security audits
Have you had an independent review of the actual security level of your core applications? How does a real hacker exploit my business? Are your application protected against the OWASP top 10 (Injection, Broken authentication, Sensitive data exposure, XML External Entities, Broken access control, Security misconfiguration, Cross-site scripting, Insecure deserialization of user input, Components with known vulnerabilities, Insufficient logging/monitoring)
Secure software development
Is your code regularly scanned for vulnerabilities? Are you running automated tests to avoid new code breaking existing functionality? Is each deployment such a big block that it often breaks something? Are you scanning libraries and dependencies of your code on vulnerabilities?
Zero trust
Have you identified your protect surface? How easy is it for an attacker to do lateral movement within your systems once they get a first step in? Have you mapped the different existing information flows? Do you implement segregation of duties?
Security monitoring
Do you have a security information and event management (SIEM) in place? Are you monitoring unsuccessful login attempts? Are you notified if your website suddenly loads resources from other websites to compromise your visitors? Do you have a security baseline? Is your infrastructure properly being monitored to detect inconsistencies?
Data privacy compliance
Do you have an internal data processing register? Have you appointed a data protection officer (DPO)? Are you aware about the data breach notification obligations and their deadlines? Are your services GDPR compliant? Are you properly handling data subject request? Are you properly collecting data subject consents? Have you conducted data impact analysis?
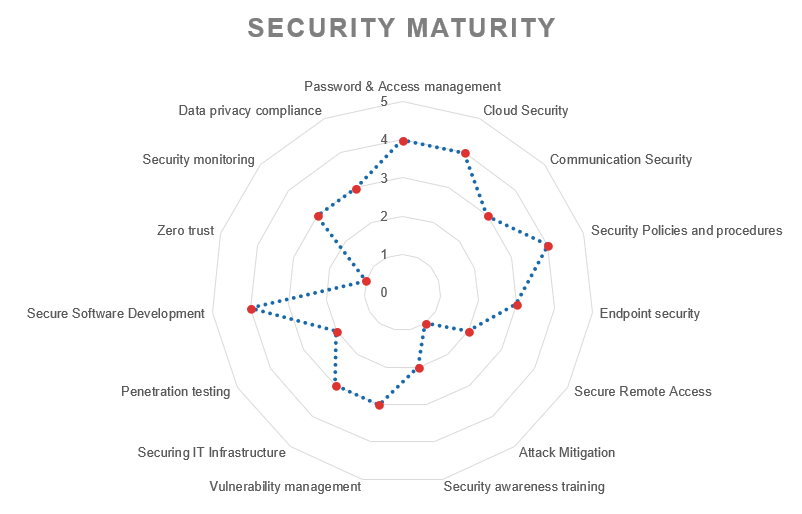
See your security mature
You'll get a monthly report to see the evolution of each of these core security areas, including a detailed list of actions that have been taken.
Interested
Let's have a call and see how we can help your business grow securely